Back to Basics: Demystifying Email Security Protocols
While SPF, DKIM, and DMARC may seem like basic concepts, many organisations still don’t have them configured correctly, and many people (both technical and non-technical) aren’t familiar with how they work. For those in security operations who regularly handle phishing and spoofing attempts, understanding these protocols is critical to maintaining a secure email environment. That said, they are valuable for anyone looking to strengthen their email security. Let’s revisit these foundational protocols to better understand how they contribute to a strong security posture.
Introduction
Picture this: Two grand kingdoms, each ruled by a wise king. Red and Blue—these monarchs have important messages to send to one another.
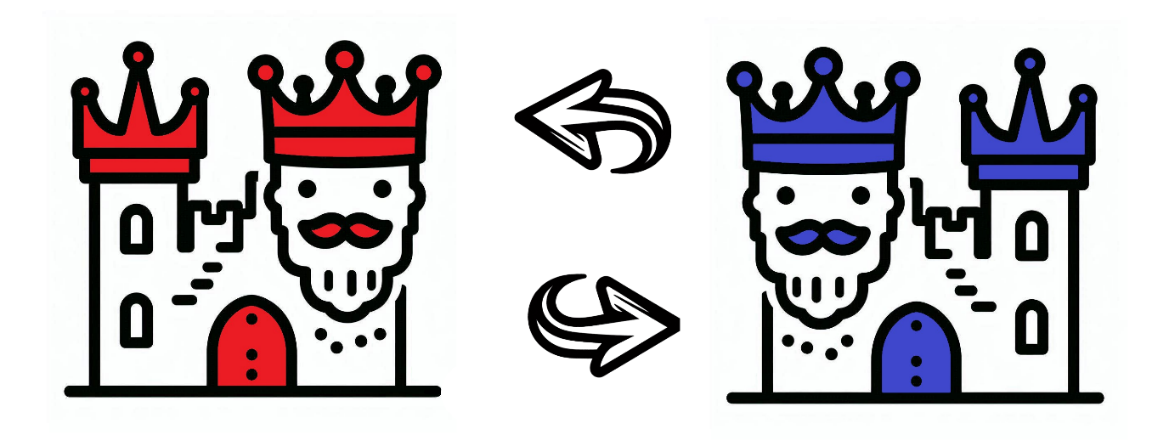 But how can they ensure their messages reach the right king without being intercepted, tampered with, or sent by imposters? The answer lies in a trusty trio: colourful messenger pigeons, wax seals, and The Postmaster.
But how can they ensure their messages reach the right king without being intercepted, tampered with, or sent by imposters? The answer lies in a trusty trio: colourful messenger pigeons, wax seals, and The Postmaster.
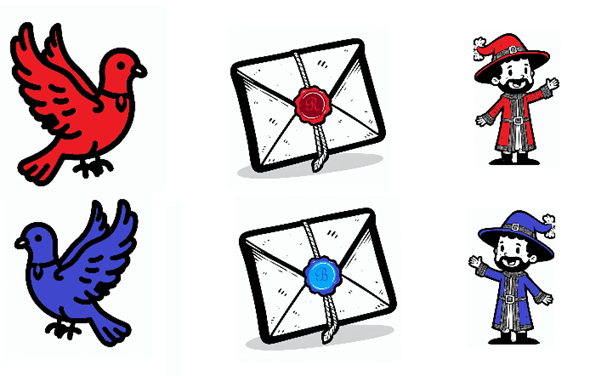
In the world of email security, we call these protectors SPF, DKIM, and DMARC, and they’re here to defend your inbox.
While kingdoms may sound like a fairy tale, the challenges of secure communication are all too real in the digital world. Email security is crucial to prevent fraud, phishing, and spam from infiltrating inboxes. In this article, we’ll break down three key protocols—SPF, DKIM, and DMARC—using our two kings and their trusted systems to explain how they work together to protect your emails.
SPF (Sender Policy Framework)
Let’s begin with the first layer of protection—our trusty messenger pigeon. Each king sends their messages using a pigeon that matches their kingdom’s colour. The Red King sends red pigeons, and the Blue King sends blue ones.
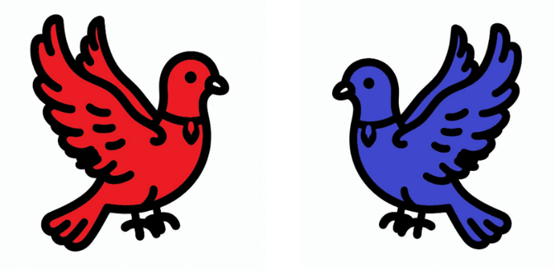
If a letter arrives carried by a pigeon of a different colour, the recipient knows something’s wrong. In the world of email, this pigeon is SPF—the first line of defence that checks if the email really comes from an authorized source.
In the real world, SPF (Sender Policy Framework) works in a comparable way. Domain owners publish a list of authorized mail servers in the DNS (Domain Name System), which says, ‘Only these mail servers are allowed to send emails on behalf of my domain.’ When an email arrives, the receiving server checks the SPF record to make sure the message is coming from an approved source—just like checking the pigeon’s colour.
Imagine the Blue King receives a message carried by a green pigeon. Immediately, the Postmaster is suspicious—this pigeon does not belong to the Red King.
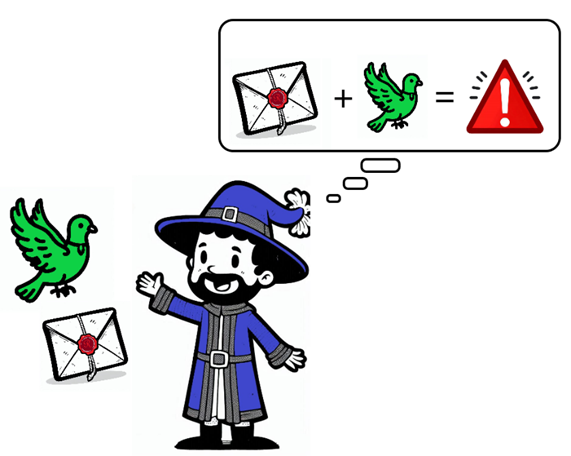
Similarly, when an email’s source does not match the list of approved senders in the SPF record, the email gets flagged or rejected. SPF helps prevent email spoofing, where malicious actors pretend to send emails from a trusted domain.
Let us say the Blue King (your company) is expecting a message from the Red King (your business partner’s domain). If the message comes via a red pigeon (an authorized server in their SPF record), all is well. But if it arrives on a suspiciously green pigeon (an unapproved mail server), the Postmaster does not pass the letter on to the Blue King. In practice, SPF can stop forged emails that attempt to trick recipients by pretending to be from legitimate domains.
DKIM (DomainKeys Identified Mail)
Now, even though the pigeon’s colour helps identify where a message comes from, how can the receiving king be sure that the message was not tampered with on the way? This is where the wax seal comes in.
 Each king uses a distinct seal to mark their letters, ensuring that the message inside is authentic and has not been altered. In the world of email, this wax seal is represented by DKIM (DomainKeys Identified Mail).
Each king uses a distinct seal to mark their letters, ensuring that the message inside is authentic and has not been altered. In the world of email, this wax seal is represented by DKIM (DomainKeys Identified Mail).
In technical terms, DKIM adds a digital signature to each outgoing email. This signature is unique to the sender’s domain and is encrypted in a way that ensures the message hasn’t been changed during transit. Just like the wax seal on a letter proves that it was sent by a specific king and hasn’t been tampered with, DKIM ensures that the contents of an email are authentic and intact.
When a message arrives, The Postmaster checks the wax seal. If the seal matches the one they expect from the sender, the letter is accepted. If the seal is broken or doesn’t match the known pattern, the message is rejected or flagged as suspicious. Similarly, when an email arrives, the recipient’s mail server checks the DKIM signature against the sender’s public key (published in the DNS). If the signature matches and hasn’t been altered, the email is considered valid.
Picture this: The Blue King sends an important message sealed with his distinctive wax stamp. When the message reaches the Red King, The Postmaster checks the wax seal.
 As long as the seal is unbroken, the Red King knows the message is genuine. But if the seal is tampered with or bears an unfamiliar seal, he’s immediately on alert.
As long as the seal is unbroken, the Red King knows the message is genuine. But if the seal is tampered with or bears an unfamiliar seal, he’s immediately on alert.
In email security, DKIM serves the same purpose. It verifies that the email content hasn’t been altered during transmission, making it crucial in preventing man-in-the-middle attacks or forged content.
DMARC (Domain-based Message Authentication, Reporting & Conformance)
Even with the right pigeon and an intact wax seal, how do the kingdoms decide what to do when something doesn’t add up? This is where The Postmaster steps in. Each king relies on The Postmaster to oversee the process of receiving messages. They’re responsible for checking both the pigeon’s colour and the wax seal, ensuring the message is legitimate. If something seems off—say a red pigeon delivers a letter with a broken seal—the Postmaster knows what to do. In email security, The Postmaster represents DMARC, responsible for making the final decision on what happens to questionable messages.
In real terms, DMARC (Domain-based Message Authentication, Reporting & Conformance) enforces policies that combine the checks from SPF and DKIM. It tells receiving mail servers what to do when an email doesn’t pass these checks—whether to accept, quarantine, or reject the message. DMARC also sends reports back to domain owners, letting them know how their emails are being handled across the internet.
Imagine The Postmaster receives a letter that fails one of the checks—maybe the pigeon’s colour is right, but the wax seal is broken, or neither match. Should the
message be delivered anyway, held for further inspection, or outright rejected? The Postmaster knows what to do with the bad messages by referring to the established decrees from each king. In the world of email, DMARC enforces these types of policies. If a message fails the SPF or DKIM checks, DMARC tells the receiving server how to handle it. Whether it’s rejecting the email, sending it to the spam folder, or accepting it with a warning depends on the policies configured by the domain owner.
Let’s say the Blue King’s Postmaster receives a letter that passes the pigeon colour check (SPF) but fails the wax seal check (DKIM). The Red King has set strict policies that tell The Postmaster to reject any messages that fail these tests.
 DMARC works in a similar way by providing domain owners control over how their emails are handled—if a message doesn’t pass both SPF and DKIM, DMARC dictates whether it should be accepted, flagged, or blocked entirely.
DMARC works in a similar way by providing domain owners control over how their emails are handled—if a message doesn’t pass both SPF and DKIM, DMARC dictates whether it should be accepted, flagged, or blocked entirely.
Putting It All Together
Now that we’ve met our three protectors—pigeons, wax seals, and The Postmaster—let’s see how they work together to keep the kingdoms’ communications safe. Imagine the Red King wants to send an important letter to the Blue King.
 First, he dispatches a red pigeon (SPF), ensuring the message comes from a trusted source. Next, he seals the letter with his unique wax stamp (DKIM), guaranteeing that the message hasn’t been tampered with. Finally, when the letter arrives, the Blue King’s Postmaster checks both the pigeon and the seal. The Postmaster references the latest decrees (DMARC) set by the Red King to determine how to handle any messages that don’t pass inspection. If both checks pass, the message is delivered without a hitch. If not, The Postmaster follows the established rules—perhaps quarantining or rejecting the message outright.
First, he dispatches a red pigeon (SPF), ensuring the message comes from a trusted source. Next, he seals the letter with his unique wax stamp (DKIM), guaranteeing that the message hasn’t been tampered with. Finally, when the letter arrives, the Blue King’s Postmaster checks both the pigeon and the seal. The Postmaster references the latest decrees (DMARC) set by the Red King to determine how to handle any messages that don’t pass inspection. If both checks pass, the message is delivered without a hitch. If not, The Postmaster follows the established rules—perhaps quarantining or rejecting the message outright.
In the real world, SPF, DKIM, and DMARC work just like the kings’ system. SPF checks the sending mail server to verify if it’s authorized to send emails on behalf of a domain. DKIM ensures that the content of the email hasn’t been altered during transmission. DMARC enforces the domain owner’s policies, deciding what happens to emails that fail SPF or DKIM checks. Together, these protocols help prevent phishing, email spoofing, and other forms of email fraud, making sure only legitimate messages get through.
Conclusion
In the digital world, securing your emails is no less important than protecting royal communications between kingdoms. With SPF, your emails get the right colour pigeon to verify their origin. DKIM adds the wax seal to ensure the message remains intact. Finally, DMARC oversees everything, making sure only legitimate, trusted messages reach their destination. Together, these protocols form a powerful defence against email threats.
With phishing and email spoofing becoming increasingly common, implementing SPF, DKIM, and DMARC is critical for protecting your domain from being used in fraudulent schemes. By configuring these protocols, you’re not only securing your own communications but also safeguarding the trust your customers and partners have in your brand. Without them, your organization’s email reputation could be at risk.
Now that you’ve been introduced to these three royal protectors of email security, it’s time to make sure your domain is well-guarded. Whether you’re managing a small business or a large enterprise, review your email security settings, implement SPF, DKIM, and DMARC, and protect your inboxes like a king! After all, you don’t need to be a king to deliver your email securely.
